HTB Web Challenge: Spookifier
Intro
There's a new trend of an application that generates a spooky name for you. Users of that application later discovered that their real names were also magically changed, causing havoc in their life. Could you help bring down this application?
Solving Spookifier
First, I downloaded the files and opened them in visual studio code. Here I noticed that:
- Mako templating was being used
from flask_mako import MakoTemplates… very interesting- https://www.makotemplates.org/
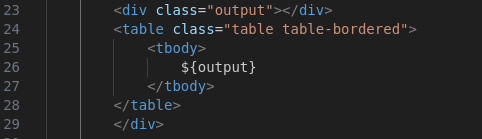
From the Mako Templating Documentation, I found the syntax for using Mako templates: ${<variable>}
${output}
Okay, so at this point it is confirmed that Mako templates are being used.
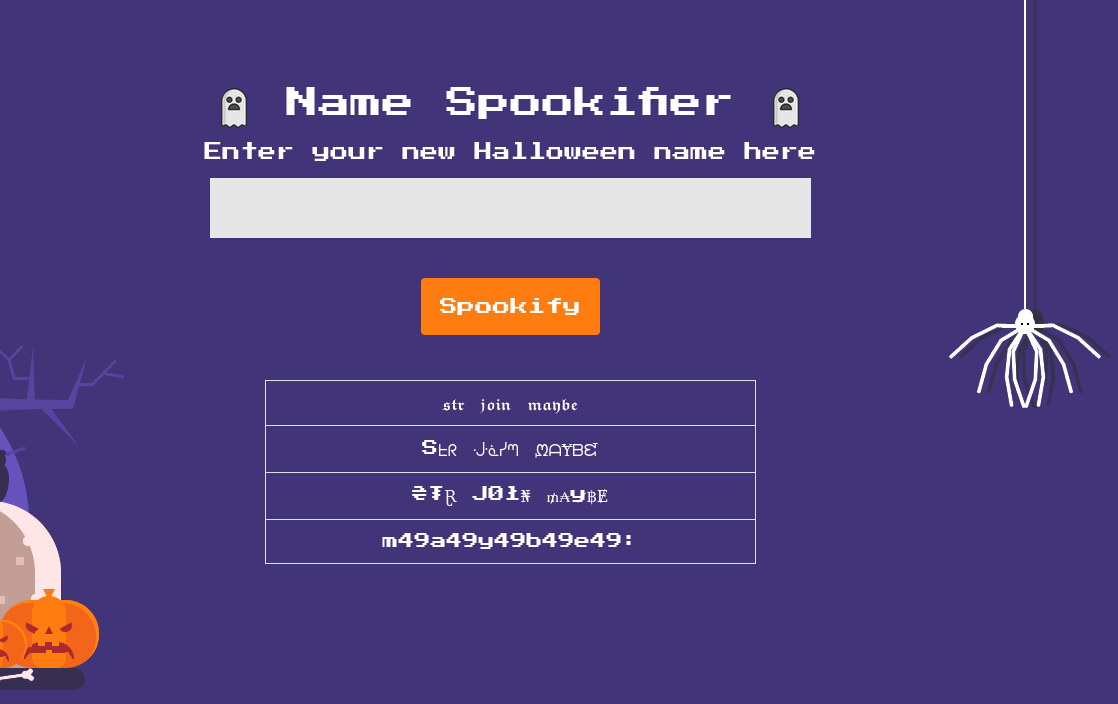
The point of this web app is take in some user input, and then Spookify it.
Based on the source code, it doesn’t look like user input is sanitized. Let’s test for a Server-Side Template Injection (SSTI)
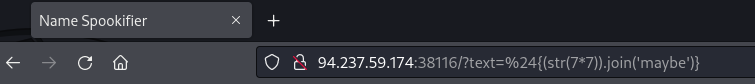
Payload: ${(str(7*7)).join('maybe:')}
At this point, it is clear that this web application is vulnerable to SSTI, but not necessarily Remote Code Execution (RCE).
The documentation for Mako templating includes a section on